
Cloud Forensics: Faster, Better, Easier with Magnet AXIOM and the Cloud Insights Dashboard
Cloud forensics, investigations that include cloud data, are becoming more common. More and more services are leveraging cloud-based, rather than local on-the-device, storage.
Magnet AXIOM is always being improved to be able to support the needs of your investigations. And, because cloud sources have become more prominent, we’ve worked to streamline your workflow and support your cloud forensics investigations.
If you haven’t tried AXIOM or AXIOM Cyber yet, request a free trial here.
Uncover More Leads in the Cloud and on the Device
Cloud forensics data recovery for specific apps and services isn’t always the easiest thing to do.
Apps and services are inconsistent when it comes to data storage, meaning it’s difficult to know what exactly is available to you and from where. Apps and services spread data between local storage on the device and cloud storage differently, which makes obtaining the appropriate legal authority to collect data from the cloud a challenge. Things are especially complicated when users have a significant number of apps and services because even uncovering which apps and services a user has access to (or has accessed on the device more broadly) can be a time-consuming process.
We’re excited to help streamline the discovery workflow with the Magnet AXIOM Cloud Insights Dashboard. Now, more cloud account information will be automatically surfaced, making it easier to identify which cloud accounts are associated with device extractions. The benefit is two-fold, the Cloud Insights Dashboard will surface the supported cloud accounts that AXIOM has uncovered a password and/or token for, giving you a lead on the apps that you can search for locally on the device, and a lead to obtain legal authority to acquire the cloud data for.
One other significant benefit of working in the Cloud Insights Dashboard is that you’ll have a prompt displaying the different access methods available for that cloud data, such as by acquiring open-source information, logging into the account to acquire data, uploading a user-generated archive, or a warrant return package. Plus, in the dashboard, you will be provided with some resources to help you determine the potential artifacts you can find for each of the identified cloud sources.
The Cloud Insights Dashboard was designed to streamline your workflow, so you will be able to launch cloud acquisition processes directly from the dashboard, while investigating your relevant cloud data all in one place. Acquiring cloud data and knowing what data is available for acquisition has never been easier.
Check out the how-to video from Trey Amick to see the Cloud Insights Dashboard in action.
Automatically Surface Passwords and Tokens
Magnet AXIOM automatically identifies passwords and tokens in the refined results.
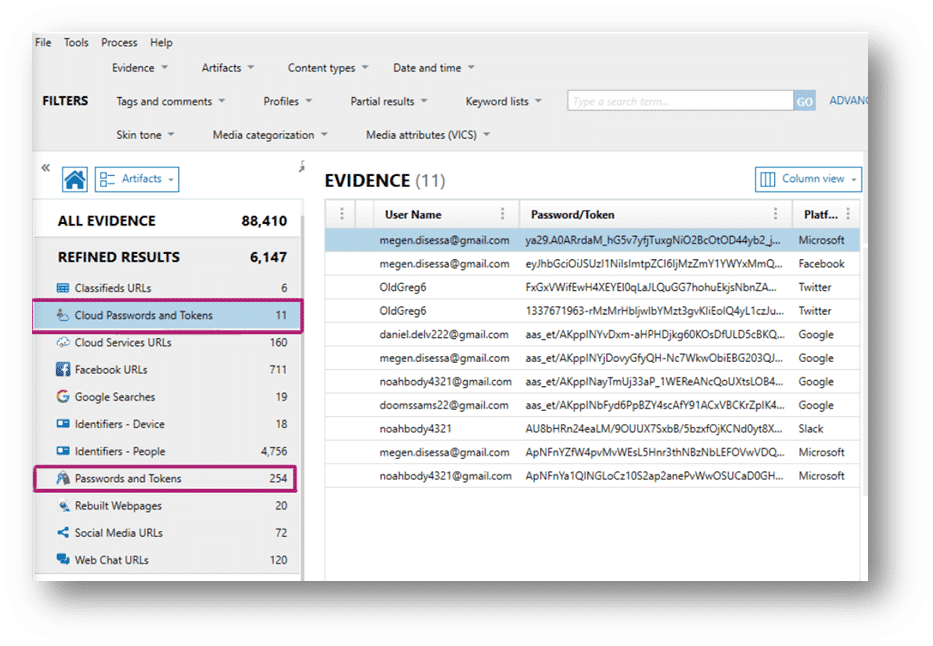
Many applications will house password and authentication tokens in their respective databases but searching each individual application for those passwords and tokens can be a labor-intensive process. Beyond that, if there’s new cloud applications that you’re unfamiliar with, it can take time to unpack how the app stores data, or what data that application may store on the device or in the cloud.
Magnet AXIOM works to search known and supported apps for passwords and tokens and brings the data to the refined results, meaning you don’t have to scour each individual app to locate passwords and tokens that could lead to case-relevant evidence.
There are two categories, “Passwords and Tokens” and “Cloud Passwords and Tokens”. The “Passwords and Tokens” category will highlight the passwords and tokens for all supported artifacts, regardless of the data source (including cloud sources). “Cloud Passwords and Tokens” is only for cloud sources, and it’s from here that the data in the Cloud Insights Dashboard is populated. So, you will see cloud passwords and tokens in both categories.
Once you have those passwords and tokens, as well as the appropriate legal authority, you can collect data from many cloud services and providers, such as the new support offered for Google Drive, for example. Artifact support for Google Drive activity has been included in AXIOM 6.0, so you can now recover file activity such as: Create, Edit, Move, Rename, Delete, Restore, and more.
Recovering and Analyzing Data from Vendors Such as Apple
iPhones, Macs, and iPads are some of the most popular devices and so recovering user data from Apple is a common aspect of many investigations. We have provided a few tools to support your Apple cloud data investigations, such as the MAGNET Apple Warrant Return Assistant, which is a one-click solution that downloads, decrypts, and decompresses all the data from the individual links provided by Apple for warrant returns. The assistant then wraps all of that data into a single .zip file that can be processed by Magnet AXIOM.
Grab a copy of the MAGNET Apple Warrant Return Assistant on our Free Tools page.
With Magnet AXIOM, you can also recover iCloud backups for devices running up-to and including iOS 15. Giving you more options to be able to recover data from Apple with ease, whether it’s via live-acquisition, user-generated archives, or warrant return.
Check out this blog from Kim Bradley on how to analyze iCloud backups.
Cloud Investigations Offer New Opportunities
Overall, collecting data from cloud services can provide you with a unique opportunity to work with consenting victims to collect “download your information” type packages. Sometimes victims may be more open to providing consent for specific apps or services because they may have more control over the information they share, while also being able to keep their mobile devices. Letting victims know that there could be an opportunity to be more prescriptive about what they share, allowing them to maintain some of their privacy regarding specific aspects of their cloud accounts or services, may help overcome some concerns victims have about sharing data.
Many challenges still confront investigators when it comes to cloud investigations, but with Magnet AXIOM there are steps being taken to at least reduce the obstacles when it comes to data recovery and analysis. Check out the Magnet AXIOM Cloud Forensics page to learn more about the cloud data you can recover and analyze with Magnet AXIOM.