Digital Forensics: Artifact Profile – Google Chrome
APPLICATION NAME: Google Chrome
CATEGORY: Web Related
RELATED ARTIFACTS: Chrome Web History, Chrome Web Visits, Chrome Sync Data, Chrome Sync Accounts, Chrome Session/Tabs Carved, Chrome Last Tabs, Chrome Current Tabs, Chrome Last Session, Chrome Current Session, Chrome Top Sites, Chrome Logins, Chrome Searches, Chrome Keyword Search Terms, Chrome History Index, Chrome FavIcons, Chrome Downloads, Chrome Cookies, Chrome Cache Records, Chrome Bookmarks, Chrome Archived Web History, Chrome Archived Keyword Search Terms, Chrome Autofill, Chrome Autofill Profiles, Chrome Saved Credit Cards
OPERATING SYSTEMS: Windows, Android, iOS, Linux
SOURCE LOCATION:
Windows – %root%\Users\%username%\AppData\Local\Google\Chrome\User Data\Default
Android – data\data\com.android.chrome\app_chrome\Default
iOS – %root%\Library\Application Support\Google\Chrome\Default
Linux – /home/$USER/.config/google-chrome/
Importance to investigators
According to Statcounter.com, as of 2024, Chrome still dominates the web browser market with 65.68% of the overall market[i]. It is available for all major platforms, and it is very likely examiners will come across Chrome in one of their investigations, if not most of them.
Like most browsers, Chrome stores much of its history data in a database while storing cache data, such as pictures, webpages, scripts, cookies, etc., in a nearby folder. The history is typically stored in SQLite databases under the user’s AppData folder in Windows and uses a similar format for Linux, iOS, and Android. Beyond the history, cache, bookmarks, and cookies you’ll find with most browsers, Google Chrome stores sync data, tab/session data, login information, and many other sources of evidence that may be useful to examiners.
Google also offers Chromium as an open-source framework that many other third-party browsers use as a back-end. This explains why examiners may notice some similarities between Chrome and other browsers in how the data is stored and what is available to their investigation. Chrome uses the Blink engine, which is shared with certain versions of Opera, Vivaldi, and Microsoft Edge. While visually different from the user, many of these browsers are the same on the back end. This is great from an analysis standpoint as they are stored similarly. However, once you start carving deleted records, you might find it hard to ascertain which browser the data came from. This is why you’ll often see carved records for these browsers all bunched together.
Google Chrome recovery with Magnet Forensics
Browsing History
The primary source of evidence for Google Chrome is the history database located under the Chrome user’s profile, and there are several areas of interest to investigators:
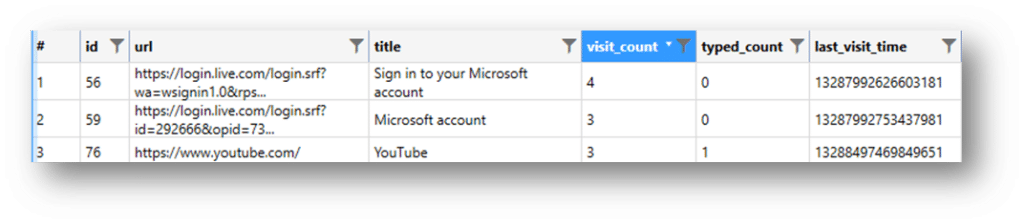
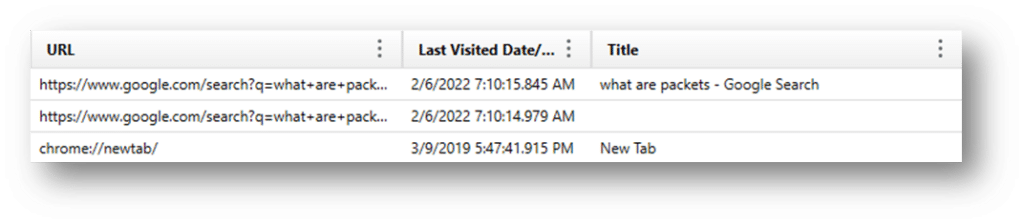
URLS – The urls table contains the basic browsing history for Chrome. This will include a single instance for all the URLs visited, a timestamp for the last time visited, and a counter for the number of times visited. This is the URLs table (SQLite):
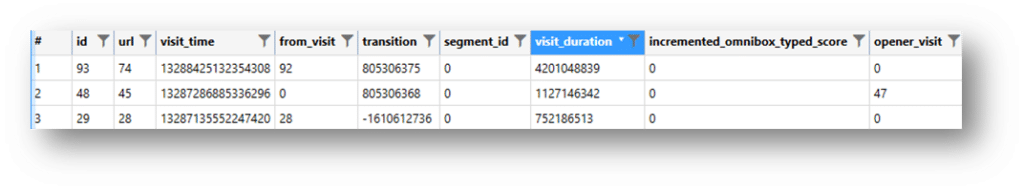
VISITS – The visits table in browsers using Chromium will contain multiple records for the same URL each time the page is visited. A user may have several records for “magnetforensics.com,” and the visits table will list each time it was visited along with an additional timestamp for each visited page. The additional timestamp is the positive value; however, the challenge is that the actual URL isn’t listed in this table—only a pointer to the matching record in the URLs table mentioned above. This means that the two tables must be joined if you’re manually analyzing the data. Any tool that carves deleted records must find the matching record in a separate table, or you may be left with partial results. This is the Visits table (SQLite):
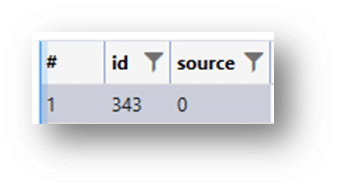
VISIT_SOURCE – The visit_source table allows you to identify where a given URL came from. Just because a URL was listed in the database does not necessarily mean that it was browsed on that given computer. Many browsers, including Chrome, allow data to be synchronized across devices so that your browsing experience is uniform whether you’re on your computer or mobile device. The visit_source table must be joined with the urls and visits tables to map out the entire history including the source of a given url (whether it was browsed locally, synced from somewhere else, or imported from another browser, etc.) The “source” column utilizes the following definitions:
- 0: SOURCE_BROWSED
- This indicates that the visit originated from direct navigation by the user, such as typing a URL in the address bar or using a bookmark.
- 1: SOURCE_LINK
- This denotes that the visit was a result of clicking on a link from another webpage.
- 2: SOURCE_TYPED
- This signifies that the visit resulted from the user typing the URL directly into the address bar.
- 3: SOURCE_BOOKMARK
- This means the visit came from a user clicking on a bookmark.
- 4: SOURCE_EXTENSION
- This indicates that the visit was initiated by a browser extension.
This is the Visit_Source Table (SQLite):
Axiom parses these databases from their SQLite format into easily read/understood formats:
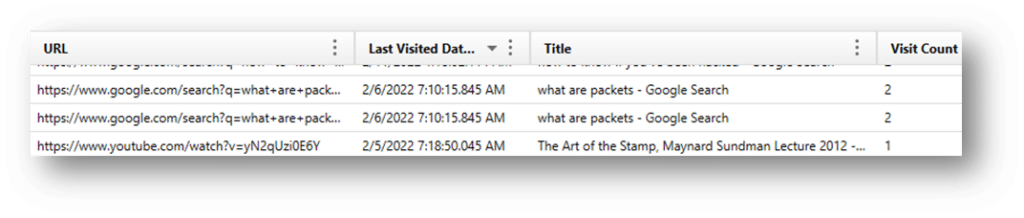
Chrome sync data, Chrome sync accounts
Google synchronizes data across multiple devices so that users can consolidate their browsing experience across all their devices such as computers, phones, tablets, etc. This will allow examiners to view bookmarks, history, and other browsing data that might have been created on other devices, not necessarily the one being examined.
Along with the source history information, there is an additional database of value that examiners should make use of called SyncData.sqlite. This will contain additional sync data, such as account information and devices syncing through the user’s Google account. Here, Axiom shows what an example of the parsed data looks like:
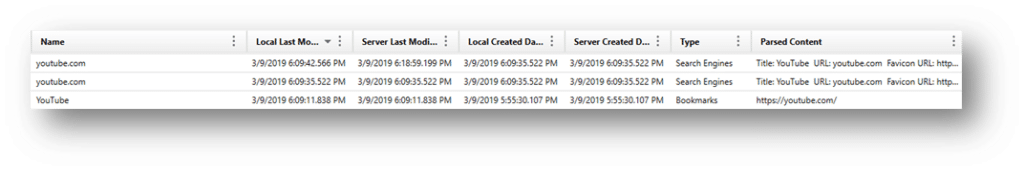
Cached Browsing History
Most web browsers cache content from the sites that users browsed to, including pictures, text, html, javascript, etc. Historically, this was used to avoid downloading the same images and content repeatedly when the same sites are visited frequently. Chrome stores cache content and information in three files: index, data_X, and f_XXXXXX files, all under the cache folders. The data_X files will store cached content if the data is small, but if it’s a larger image or other content, it will be pushed out to the f_XXXXXX. Here are examples from Axiom of the two storage locations:
Cookies
Chrome Cookies are like any other browser. They are created when browsing through the Chrome browser.
Google Analytics (GA) cookies are slightly different and can appear in any browser, not just Chrome. They are created from sites using Google Analytics to track their website stats and usage information. GA cookies can contain valuable information for examiners.
Incognito/Private Browsing
Unlike some browsers with a private browsing mode/feature, Chrome never writes the history to disk. That means if the user used incognito mode, the only source of browsing evidence would be found in memory or, by extension, the pagefile or hibernation files. Carving incognito history from memory isn’t difficult if you can acquire the data from a live system. Memory is volatile, and the data will be lost when the system is powered down.
Additional Artifacts of Interest
Chrome Current Session/Tabs – If you are examining a system that still has an active session available, Chrome will store the browsing activity here under current session and if there are multiple tabs open it will store it under current tabs. Here’s a good overview of what’s included in each:
- Current Session (contains the data from forms in the pages in the current session)
- Current Tabs (contains a list of URLs for the tabs in the current session)
- Last Session (same as Current Session, but for the previous session)
- Last Tabs (same as Current Tabs, but for the previous session)
Again, Axiom parses these tables into an easy to read format:
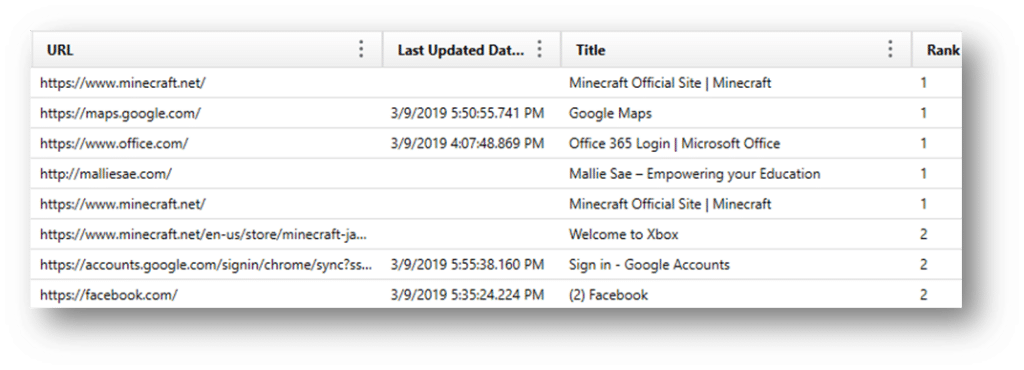
Chrome Top Sites – Chrome shows the user the most frequently visited sites in panels on a homepage, which allows the user to quickly click on a frequently visited site. We recover the data around any URL listed as a “Top Site” in Chrome.
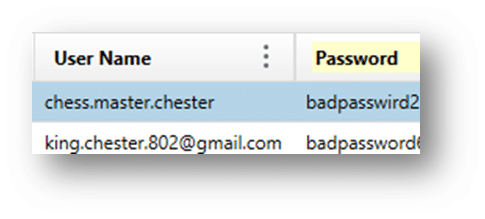
Chrome Logins – Chrome often stores usernames and passwords for some sites, so this can be recovered. Frequently, the passwords are encrypted, so you might not get those unless you are examining a live system, but otherwise, this is available if the user saves any of the data. From test data the following passwords were located (unencrypted):
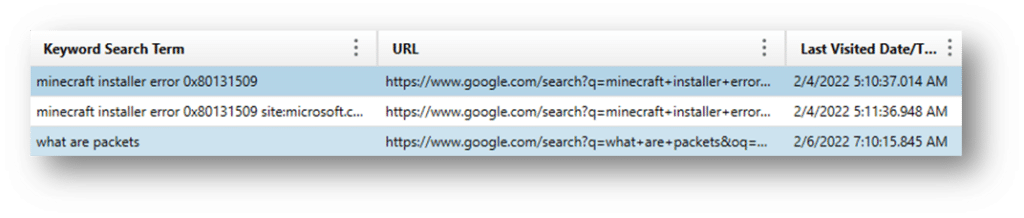
Chrome Searches/Keyword Search Terms – Chrome stores the searches done on a webpage by using the “Find” bar. So if a user hits CTRL+F, and search for a keyword on a webpage, it will be stored here. Depending on the settings in the browser this may or may not be saved across sessions.
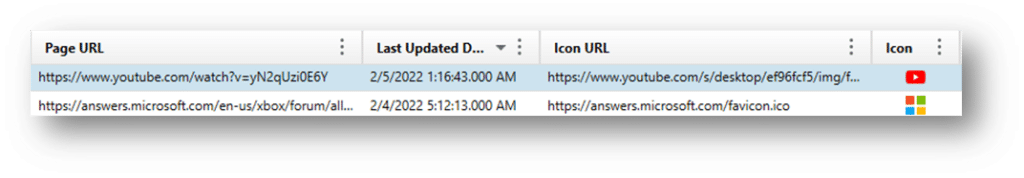
Chrome FavIcons – A favicon is a small icon associated with websites, typically displayed in browser tabs, bookmarks, and address bars. These FavIcons are stored in the SQLite database “Favicons.” The following activities can cause a favicon to be stored:
- Visiting a website
- Bookmarking a page
- Saving a page to the home screen
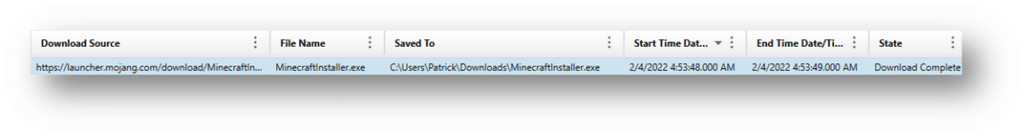
Chrome Downloads – These are downloads the user has initiated through the Chrome browser.
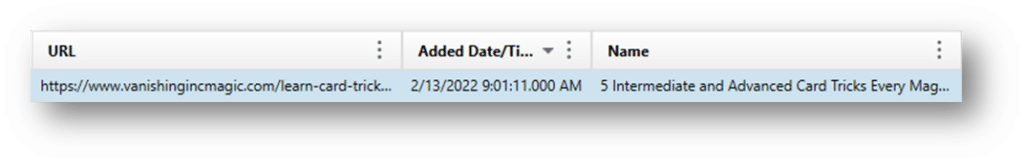
Chrome Bookmarks – Like most browsers, bookmarks are saved pages that the user or application creates to quickly visit frequently accessed sites.
Chrome Autofill/Autofill Profiles – Chrome stores field data the user has previously inputted for particular websites here. For example, if you visit “magnetforensics.com” and login to the Customer Portal, browsers will automatically save your username (or other details) so that you don’t have to type it in each time you visit the site. This data is stored in the autofill location and can be useful to help recover usernames and other details that your user has filled out on various sites.
In conclusion, the comprehensive analysis of Google Chrome artifacts is indispensable for Investigators. These artifacts, ranging from browsing history, Chrome sync data, and accounts to cached browsing history, cookies, current sessions, top sites, logins, favicons, downloads, and search terms, collectively provide a robust framework for reconstructing user activities and intent. By examining these artifacts, investigators can uncover crucial evidence, trace user behaviors, and establish timelines that are pivotal in both criminal investigations and civil disputes. The detailed insights garnered from Chrome’s rich data ecosystem underscore its significance in the digital forensics landscape, offering a window into the user’s online interactions and helping to piece together the digital narrative with precision and accuracy.
Get Magnet Axiom today!
We continually improve Axiom to make it our most comprehensive digital forensic platform. When every second counts, it’s important that we do what we can to streamline the primary workflow of examiners.
If you’re already using Axiom, download the newest version of Axiom at the Customer Portal. To try Axiom for yourself, request a free trial today!
If your agency needs to perform remote collections, collect from cloud storage services, or Microsoft Office 365, check out what’s new in Axiom Cyber here.
[i] https://gs.statcounter.com/browser-market-share/