Loading Oxygen Images into AXIOM
As a continuation of our blog series around using multiple tools to be successful in your forensic investigations, this post is going to look at loading images from Oxygen into AXIOM. You can read the intro blog here which will also link to others in the series.
Oxygen allows you to archive extraction and case data into OFB files. These are not forensic images, they are case files much like how Cellebrite uses UFD files or how AXIOM stores its case data in a SQLite database with an MFDB extension. These OFB files are simply compressed archives that can be renamed to ZIP and viewed like any other compressed container.
Android & iOS OFB Files
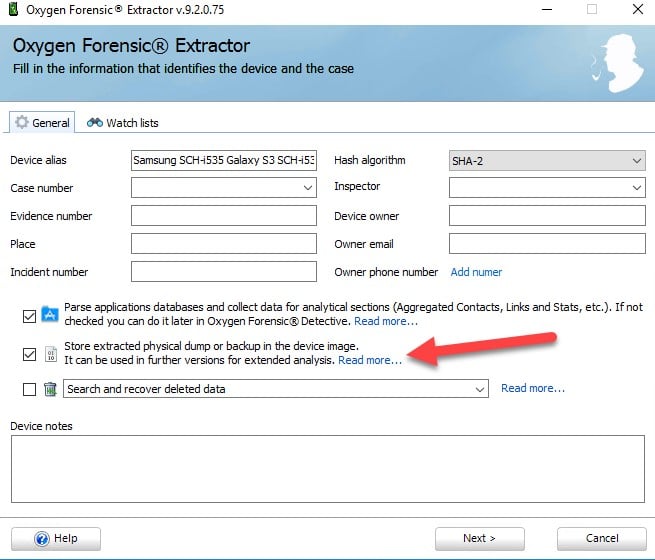
Depending on the extraction type, Oxygen does not create a forensic image of the evidence like most other tools, they will extract the files and data they need to be presented in their tool. Examiners who may want to analyze the data in other tools will want to check the box indicated below:
During an acquisition, you will have an option to include the physical dump or backup with the extraction. This is necessary in order to conduct analysis with any other tool, otherwise you will only get files specifically created or known by Oxygen. The default storage path for these images are under
ROOTUsers%USERNAME%AppDataRoamingOxyForensicsPhones
By renaming the OFB extension to ZIP, you can open up the compressed container to view the contents.
Inside this folder there are entries for each device acquired and inside those device folders is a folder called “DeviceImage” which is where the actual image is stored.
If you’ve chosen to archive the data to an OFB file, then the same structure exists with the image within the OFB archive, but it gets saved to where you choose to save the archive.
ROOTUsers%USERNAME%DesktopSamsung SCH-i535 Galaxy S3 SCH-i535 Galaxy S3 (%GUID%) %DATETIME%.ofb
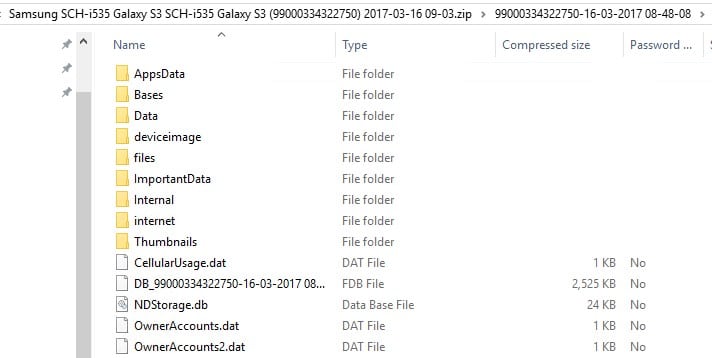
Image types
Android
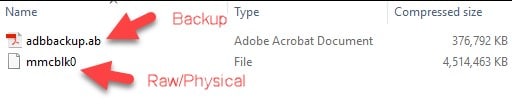
For physical images a raw/binary file gets created, these appear to be a single raw file (not segmented):
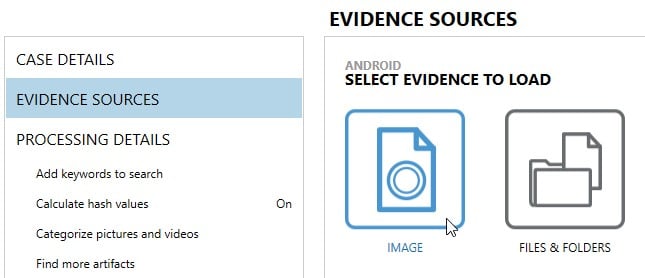
Raw BIN files can be loaded into AXIOM once they’ve been extracted from the OFB/ZIP container. Extract the files to your desktop or somewhere accessible, open AXIOM Process and choose Mobile, Android, Load Evidence, Image, and then choose the BIN file you wish to analyze.
For logical images or backups, .AB files are created which are standard Android backup images. These are compressed containers which can be opened to view the contents of the backup (opening the AB file is not necessary to load it into AXIOM, only shown here for those who are curious on how they are structured).
ROOTUsers%USERNAME%DesktopSamsung SCH-i535 Galaxy S3 SCH-i535 Galaxy S3 (990003244750) 2017-11-16 09-03.zip%GUID%-%DATETIME%deviceimageadbbackup.ab
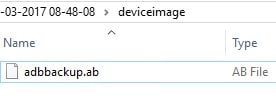
AB files can be loaded directly into AXIOM as images without needing to open them up by following the same steps above as we did for the raw/BIN files.
iOS
iOS acquisitions do not allow you to create a backup image on newer iOS devices. Most tools will provide an iTunes backup structure but it appears that Oxygen takes all the files that would normally be included in an iTunes backup and stores them within the .OFB file in their own format.
Unfortunately, there’s no easy way to load the OFB contents from an iOS backup. You could just load the ZIP as an image and it would pull the majority of the media and data that Oxygen extracted but you wouldn’t get anything more than what Oxygen found and some databases might be difficult to read. My suggestion would be to just reacquire or obtain a generic iTunes backup if you wish to analyze iOS with multiple tools. The data recovered should be similar between tools, however the format in how it is stored is completely different.
Overall, analyzing forensic images created with Oxygen with other forensic tools is relatively painless and while they use a proprietary format/extension (OFB) to create the extraction, the relevant data can still be pulled out and analyzed further with most devices.
For more details on how to load other images into AXIOM, see the other blogs in the series: Cellebrite & XRY.