
I Spy With a Drone’s Little Eye: How to Access and Examine DJI Artifacts in Magnet AXIOM
For a while now, drone data has been making its way into more and more digital forensics mobile cases. Typically, this involves either acquiring data from the drone itself (or possibly even the controller), but now they more often involve mobile devices as well. DJI, one of the most popular drone manufacturers with a reported market share of over 75%, has long been seen as one of the highest targets of drone evidence today. Unfortunately, the DJI logs found on mobile devices have moved to being encrypted for a while now.
Let’s talk more about DJI data. From the drone perspective, the on-device data has been encrypted for several versions of the hardware. From a mobile perspective, encryption of the flight logs left on mobile devices started with specific models and then rolled out to more and more of the associated drones. DJI has multiple applications for controlling and pairing with drones such as DJI Fly, DJI Go, and DJI Go 4. DJI Fly, used for most of the latest drone hardware, leaves behind several key artifacts on mobile devices that AXIOM can now help you decrypt and add even more data to your cases.
AXIOM now has the ability to decrypt encrypted flight logs that are left behind on both iOS and Android applications as well as return several other identifiers of drones that have been paired with the mobile device.
How To Access DJI Artifacts in AXIOM
To use the new DJI Log Files decryption, you’ll need to select a new prompt with AXIOM Process.
Under the CONNECTED DEVICES area of the selectable mobile artifacts, there will be a DJI artifact with a clickable [OPTIONS] link.

Selecting this [OPTIONS] link will open an important dialogue for the user to read. It should be noted the checkbox within the link is turned off by default. You MUST open the options and select the checkbox at least once to enable the flight log decryption.
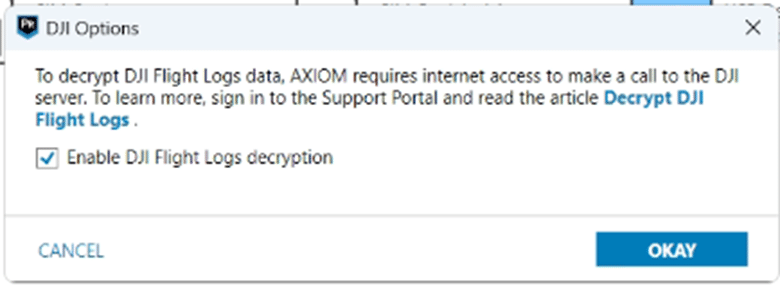
The reason for the extra steps is because to utilize the decryption, a secret key from each log must be passed online to DJI’s servers and a decryption key then returned to the AXIOM software. It is important to know that NO IDENTIFIYING INFORMATION is sent to DJI’s servers, only the required key at the beginning of the log file.
Examining the Drone Artifacts
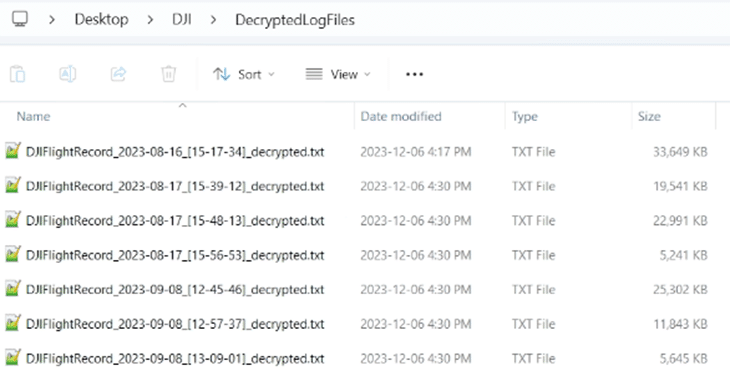
AXIOM will parse these log files into artifacts but will also store the decrypted logs for examiners to be able to do a thorough manual review. These will go to wherever your default location for temporary files is set, and by default, they will be in the case folder called “DecrytedLogFiles.”
The artifacts returned from parsing DJI app data will be found under the CONNECTED DEVICES section within AXIOM Examine’s Artifact Explorer.
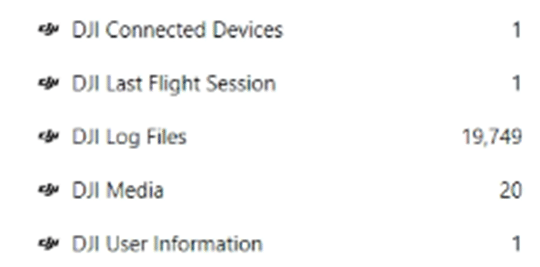
For Android devices, depending on the version of the application within the mobile evidence, some artifacts may be missing due to the separate encryption of preference files of the mobile app. DJI Log Files and DJI Media should be unaffected by this.
The DJI Connected Devices artifact will show what drones have been connected, their hardware identifiers, and when they were last connected.
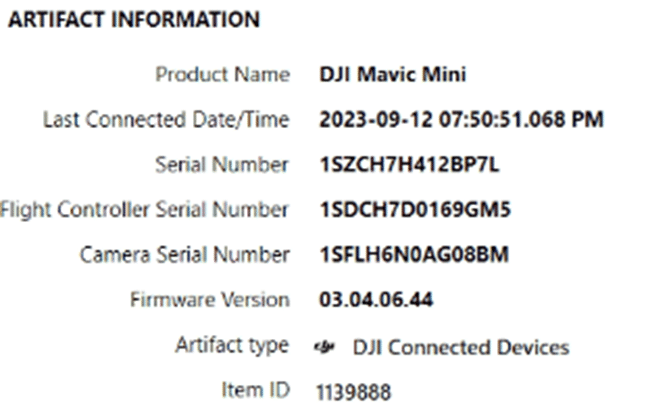
The DJI Last Flight Session is very valuable for the fact it keeps the total flights which can help determine if there are flight logs missing from the mobile device.
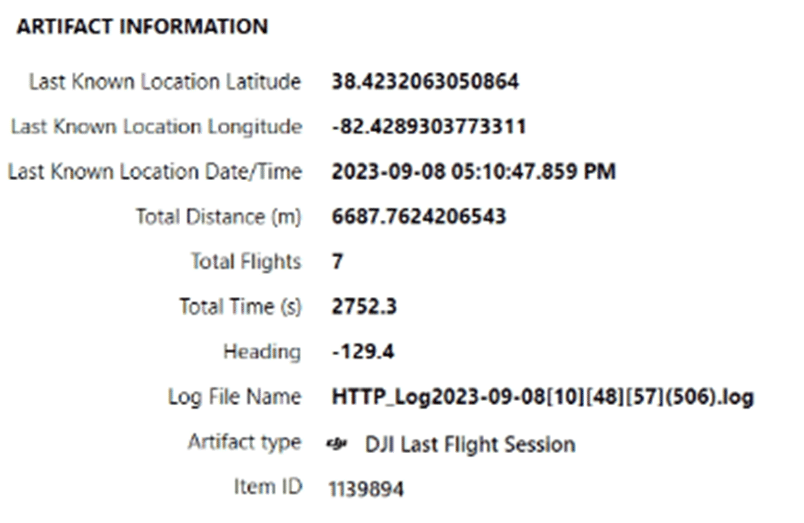
The bulk of the data will be from the DJI Log Files artifacts. While these can be reviewed in views such as Column view, more context can be gained by viewing this artifact within World Map view.
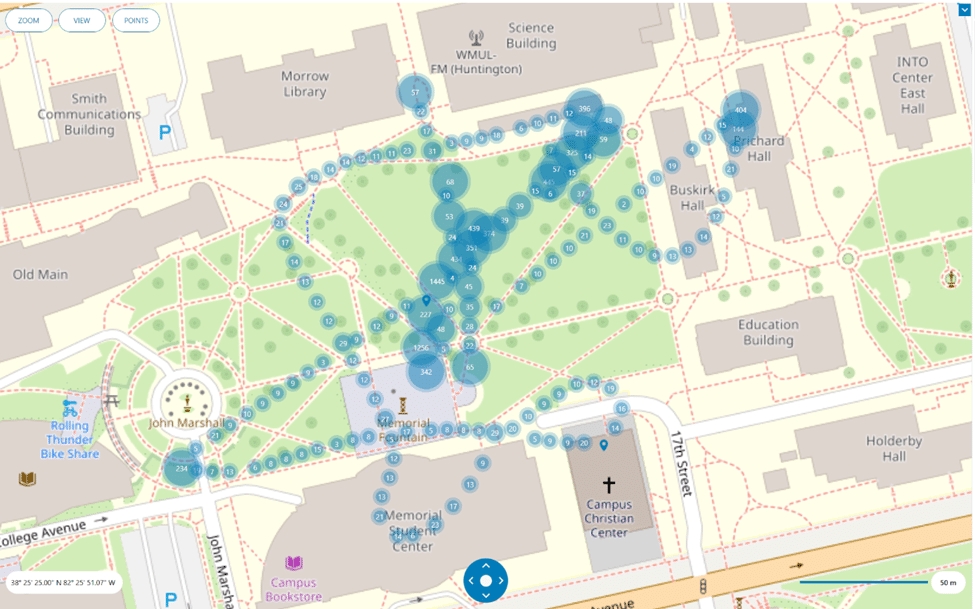
By reviewing the data in World Map view, users can plot and track the path of the drones throughout their flights. By selecting a singular point, even more data can be gathered about it.
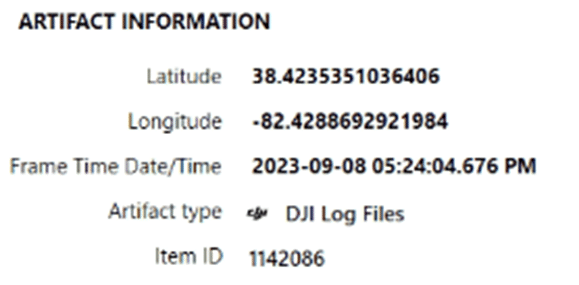
The Frame Time Date/Time can be used to manually review additional data in the logs such as speed.
The DJI Media artifact combines photos and videos from several sources into a singular artifact for review. The “File Name” fragment denotes where the data was pulled from.

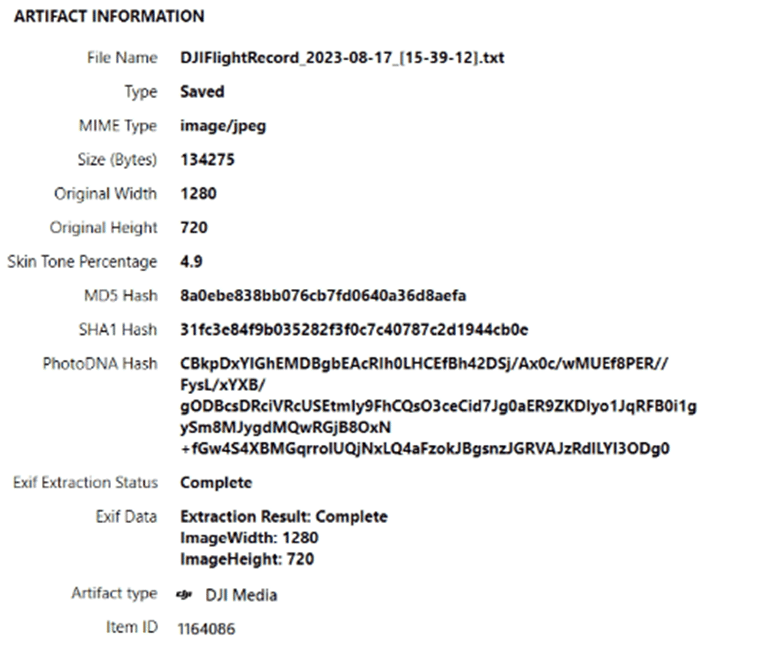
Some files will indicate they came from a flight log file as the media can be extracted from the decrypted flight logs when the data is captured during flight. This will include media that was captured during the flight and potentially not saved permanently to the mobile device’s gallery or camera roll. In addition, there may also be cached data within the app denoted by the “Type” fragment. These cached videos are not necessarily saved videos by the user but can be very valuable as they may allow you to capture video of your drone pilot during a takeoff/landing.
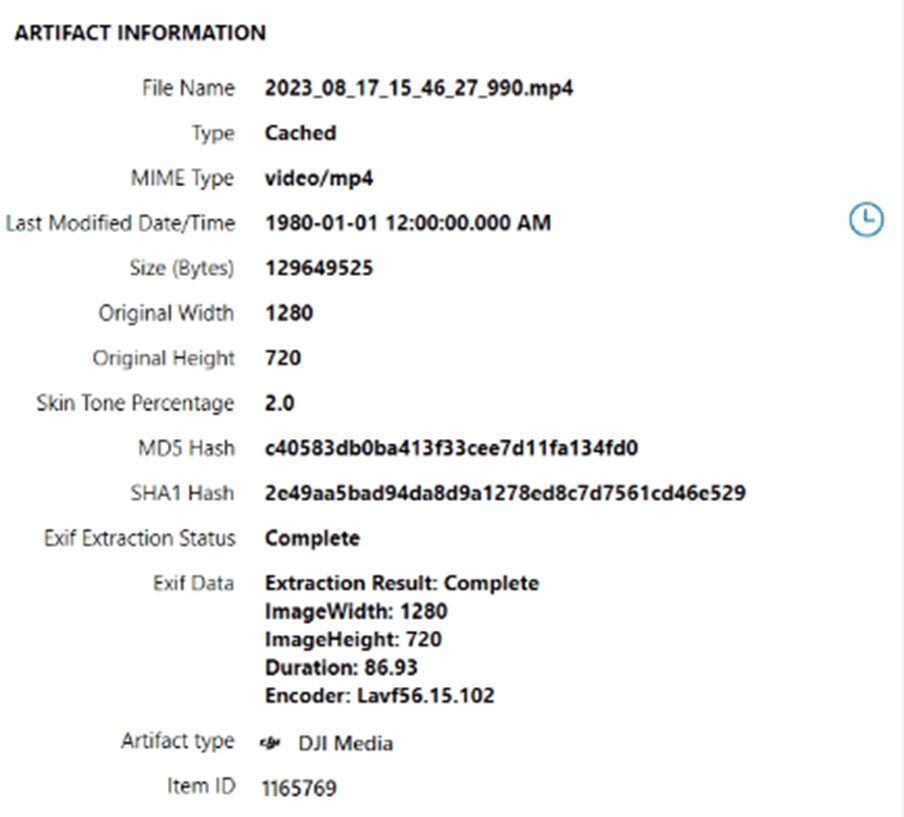

What is interesting to note about cached videos is that within testing, cached videos were found from flights where zero media was captured during the runs.
Keeping an Eye on Drone Data
As drones continue to fill news stories around the world for their variety of uses, it is important to remember that the drone itself is only part of the puzzle. While not every drone will sync to a standard iOS or Android device, those available most commonly will. As DJI continues to be the market leader for drones and also allowing other companies to make use of their SDK, it’s likely that these encrypted logs can pop up in more and more locations. It should also be noted that this data is very accessible to examiners as it does not require a full filesystem to capture and can even be acquired just from directly plugging the mobile device into a PC. Some of the user information, session data, and cached media will however only be returned from file system level extractions. AXIOM will continue to keep its eyes turned to the sky to continue to support this valuable data!
Get Your Free Trial of AXIOM Now
To try digging into DJI drone data for yourself, request your free trial of AXIOM today!