
macOS & iOS Photos Support with Magnet AXIOM
Within recent releases of AXIOM, we’ve added new artifacts to help examiners analyze images found on both iOS and macOS systems. Many investigations that examiners are faced with hinge on the images found during analysis of the data. These artifacts will help identify new points of interest and allow for more context to be drawn around images found during those investigations.
We can all agree that the amount of media being saved to devices is only going to continue to rise with larger storage options and cheaper price points being constantly released from Apple. For example, the latest iOS device released from Apple in April of this year, the iPhone SE, can be purchased for under $600 USD with 256GB of onboard storage. Taking our artifact-first approach methodology, we now give examiners analyzing macOS and iOS evidence additional media artifacts within AXIOM.
In this blog we’ll discuss some of the media, databases, and photo apps found on both iOS and macOS systems, and how AXIOM can help examiners narrow the focus when investigating media-rich evidence.
If you’re not already using AXIOM and want try AXIOM 4.1 for yourself, request a trial today.

Let’s start with how the end-user on both the iOS and macOS platforms interact, edit, and share their images: the Photos App, which comes standard on all installs. As an examiner, the Photos App has a bounty of forensically high value targets examiners may find interesting, but where do we find the data that resides in the app?
macOS path: /Users/<USER>/Pictures/PhotosLibrary.photoslibrary/database/Photos.sqlite
iOS Path: /private/var/mobile/Media/PhotoData/Photos.sqlite
It’s important to note if you’re reviewing the Photos.sqlite database on a live-running Mac for your own research, you’ll need to right-click on Photos Library.photoslibrary and select “show package contents” to see the Photos.sqlite
Under the Media category in AXIOM, you’ll find the artifact, Photo Albums, for both macOS and iOS. This artifact provides examiners with not only all of the albums a user has created to organize their media, but also if those albums have been shared, and who they have been shared with. As you can see in the screenshot below, the albums, “Travel” and “Family” reveal the album owner’s information, that it has been shared, and who the invitees are. We also can quickly identify that the “Travel” album has 4 pictures within it.
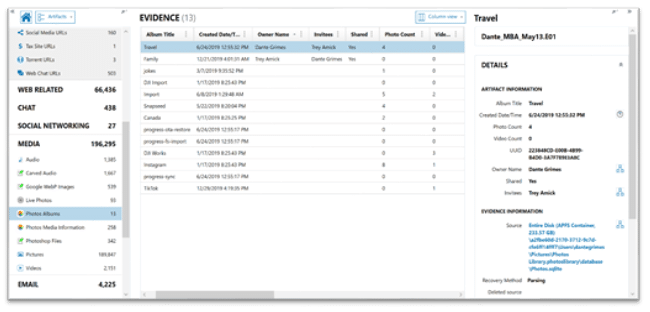
The Photos Albums artifact relies on information from the ZGENERICALBUM table found within the Photos.sqlite. Within the evidence information section of the details panel, you can review both the table and rowid for manually validating what AXIOM has revealed within artifact view. As a part of last year’s AXIOM 3.0 release we overhauled our internal SQLite database viewer. If you haven’t had the chance, make sure to check out this video on some of the updates we’ve added!
The next artifact that pulls information directly from the Photos.sqlite database is Photos Media Information. This artifact is fantastic for providing what images are found within different albums as well as the image’s UUID, which we will discuss later in this blog, and lastly geo-location data associated with the different images. In the previous screenshot, we saw the album Travel had 4 images contained with it. Below we can identify the image filenames for the Travel album.
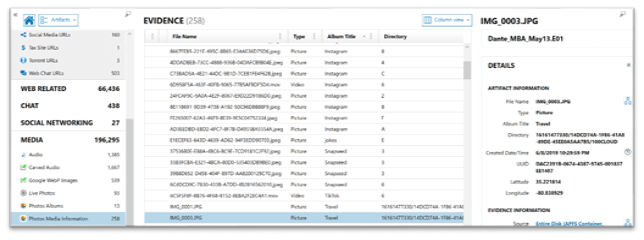
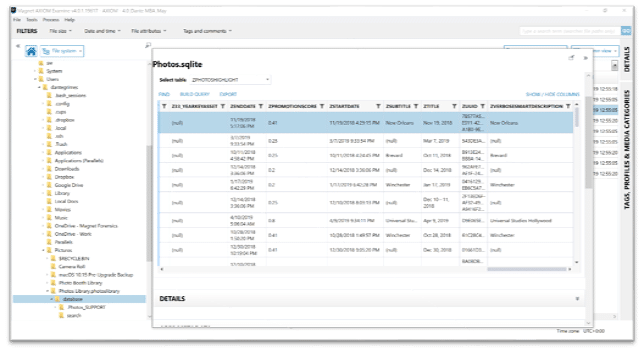
While the Photo Albums artifact only uses one table from the Photos.sqlite database, the Photos Media Information artifact pulls from several tables to help consolidate data points for examiners. Some of these tables include: ZGENERICASSET, Z25ASSETS, ZGENERICALBUM, and ZADDITIONALASSETATTRIBUTES. As we can see below, we’ve highlighted the ZPHOTOSHIGHLIGHT table from within AXIOM’s SQLite viewer to review additional information. The ZPHOTOSHIGHLIGHT table provides the description and highlight information that users can see when inside the Photos.app browsing via For You. Investigators wishing to examine the Photos.sqlite database in more depth should check out Magnet Technical Forensic Consultant Mike Williamson’s blog here.
Another important artifact for investigators to utilize when working with macOS and iOS image evidence is Live Photos. Originally launched in 2015 with iOS 9 and the iPhone 6s, Live Photos capture not only an image, but also a 1.5 second .mov movie file and can also contain sound as a part of the recording.
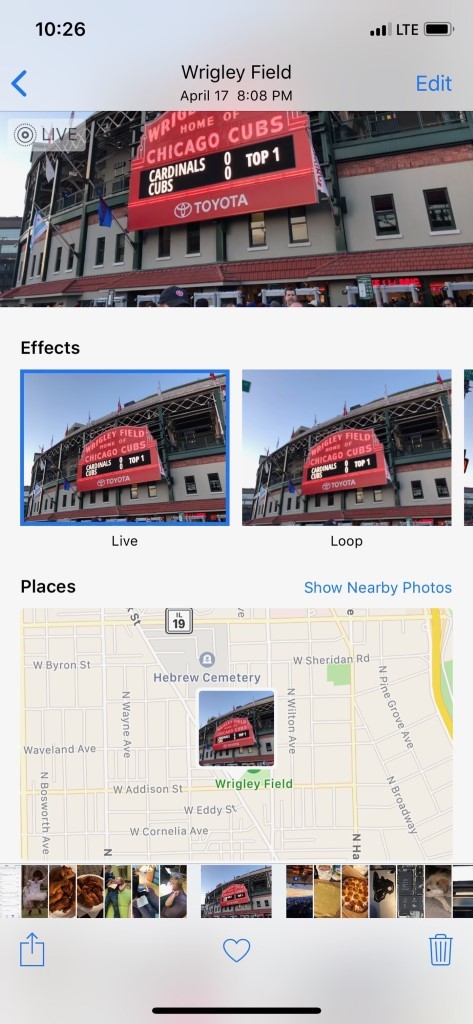

For years, investigators have had to manually review pictures separately from the potential movies that make up Live Photos; however, with AXIOM we associate the two together in one artifact. While the image and movie files typically have the same name, for example IMG_0017.JPG and IMG_0017.MOV, this always needed to be verified manually. In AXIOM, we pair the pictures and video together utilizing the matching UUID. This 32-digit UUID can be reviewed within the details panel of the Artifact explorer, or manually within the HEX in the File System explorer. As we can see below, the image in question has a UUID of 43A68D86-3DBA-472F-9804-5D1C598DBE79. We can confirm that by using the source link and reviewing the HEX as shown below.
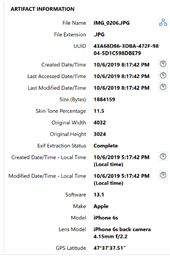
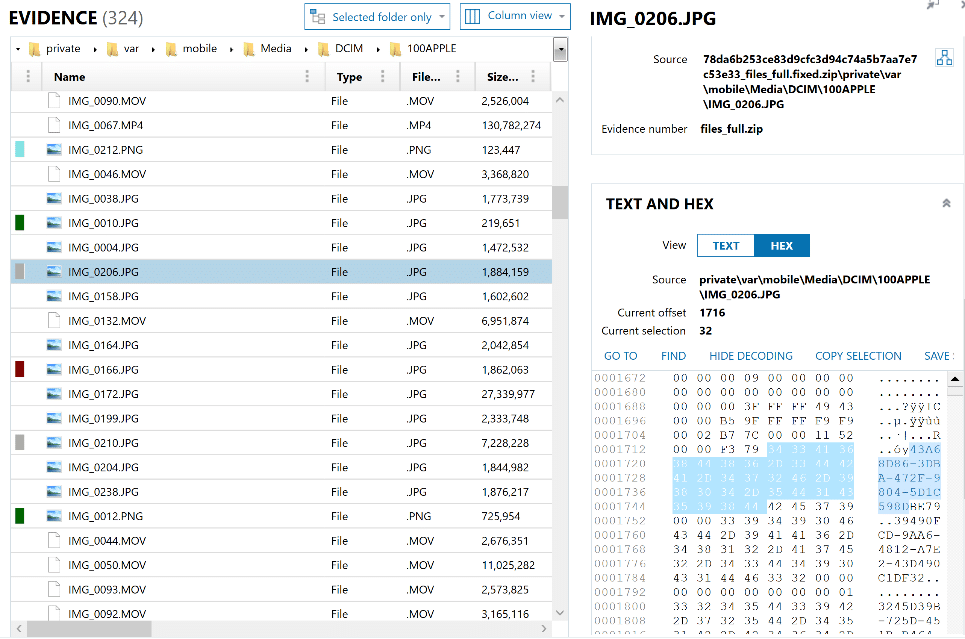
Reviewing not only the image but also the video that corresponds to that photo can allow investigators to build context around when that Live Photo was taken.
If you have any questions regarding our media support, or have ideas on artifacts you would like to see in AXIOM, please don’t hesitate to reach out to me at trey.amick@magnetforensics.com