
Leveling the Playing Field With the LevelDB View in Magnet AXIOM and AXIOM Cyber
As examiners, we are used to finding data within database files. These have often been SQLite databases which we have been examined ad nauseum to carve out every bit of data we can find. There are other types of databases out there to examine, and some that have been popping up recently that have given us trouble—including LevelDBs, which are the backend storage component for the Indexed Database API. There are also other services such as Bitcoin Core—and even Minecraft—who use LevelDBs for on-disk storage. The Indexed Database API and LevelDB format are open-source projects maintained by Google.
Several different browser clients utilize LevelDBs for storage including Mozilla, Safari, and Chrome. In fact, most all Chromium-based browsers will also use this format being based off the Chrome backbone. The purpose behind these files is to store data on the client side (aka your computer) when you’re accessing data provided from web services—sort of like we use cookies, but with much larger storage.
Not just web browsers are using LevelDBs though. Anything that’s using the Chromium engine could be storing these files. This includes things built by multiple application frameworks including Electron and Qt. Some of the more popular applications that use Chromium as part of the software are:
- Microsoft Teams
- Slack
- Discord
- Signal
- WhatsApp (dedicated app, not Windows Store variant)
Now just because these applications have the ability to store LevelDBs, it doesn’t mean it will always use them for the important data we wish to recover. It could still use other database or file formats instead. The long standing problem is how do we check? How can we use our forensic tools to explore these databases and validate what our parsers are showing us?
Using the LevelDB Viewer in Magnet AXIOM and AXIOM Cyber
There have been several upgrades and new features introduced to the LevelDB viewer in Magnet AXIOM, so be sure to update to the latest version (AXIOM 6.9 or later.). In order to use the LevelDB viewer, you’ll want to first locate your files. In a lot of the Chromium-based applications, you’re going to want to look inside the application’s IndexedDB folder as well as any “levelDB” folders.
The LevelDB viewer is looking for things such as “levelDB” in a folder name or looking for .ldb files and once you click on either the file or folder containing this data it will check to see if it’s a viewable database and show the LevelDB Viewer. At this point, it will attempt to deserialize the data within the database and render it for you in three columns: key, decoded value, and raw value. Each of these columns also offer a filter so you can search for specific values.
Taking a look at a Teams installation, you can see several LevelDB files worth digging deeper into:
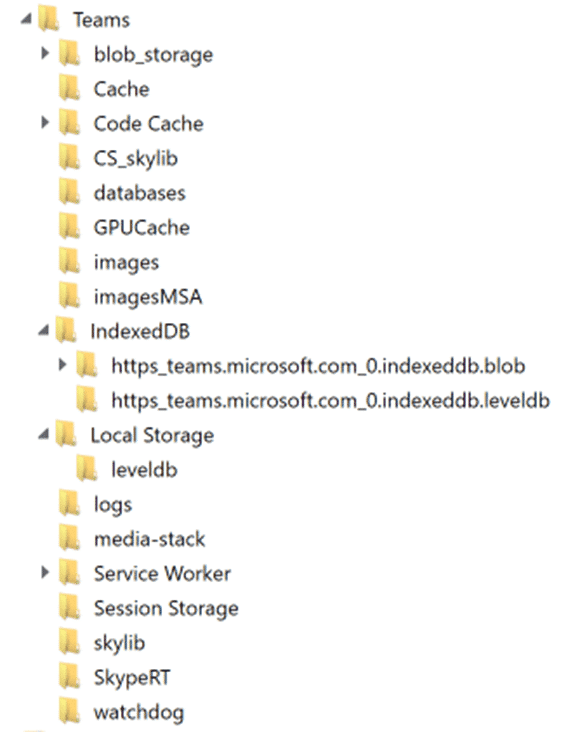
Since both the macOS and Windows versions of this application are both using that same Chromium web engine, the LevelDBs will be viewable for both operating systems.
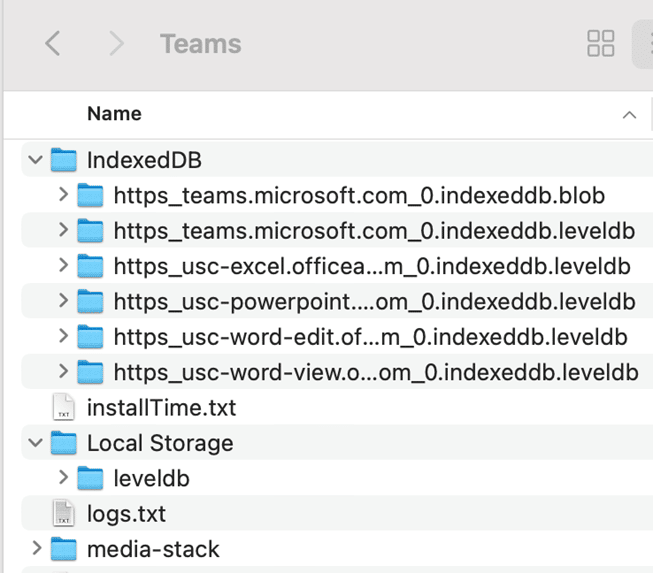
In addition, any Chromium-based browser that is used (Chrome, Brave, Microsoft Edge, etc) to visit the Teams web application will also store these LevelDB files. AXIOM’s approach to the newly revamped Microsoft Teams artifact parser is that it’ll grab that data for you regardless of the platform so long as those LevelDB files are in play.
Having a LevelDB viewer allows us to go in and validate what our forensic tools are telling us. Take for instance this message parsed out by AXIOM:
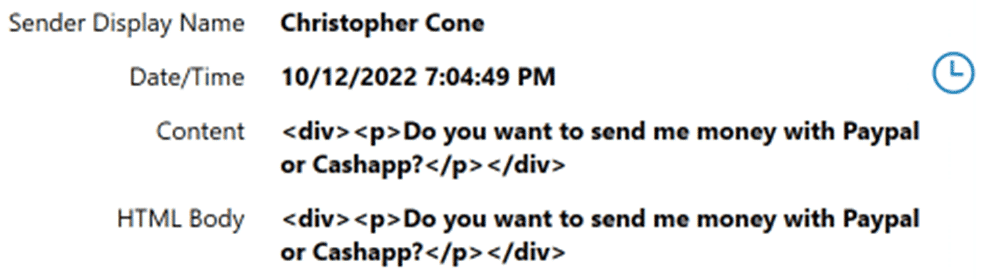

We can now see that this message was parsed from one of the “log” files within a LevelDB but going and manually finding it might be more of a headache. However, if we select the main LevelDB it came from within AXIOM, some filters built into the viewer give us a lot more power. By taking the message ID and using the find functionality within the LevelDB viewer we can see where it pops up.
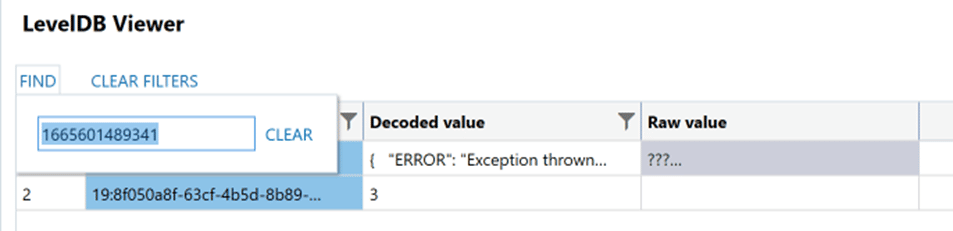
Just like the built-in SQLite Viewer, it will highlight the columns where the value was present. Many of the values in the columns may be too long to display within the viewer, so we offer several right-click options to send to other views that might help. You may see some “ERROR” values within the Decoded value column. This is because each LevelDB database can set their own custom comparator values and we have to work around this to try and find one that works best. As we continue to improve the LevelDB browser over time and as new comparators are discovered we’ll continue to reduce the amount of deserialization errors thrown. However, even if the Decoded value is not available we can still work with the Raw value data.
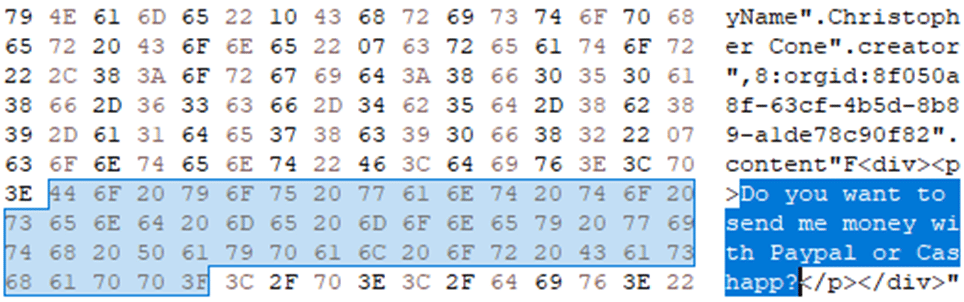
One of the right-click options allows us to just use an “Open with” function that can send the data to any tool of your choosing, and in my case, a hex viewer to see exactly what’s in the data. Looking at a snippet of the data in the hex viewer allows me to start to validate what my tools are showing me.
But what can we use the LevelDB browser for outside of validation? Well, we can use it for new artifact finding! Let’s take an artifact that’s not parsed today and see what we can do with it. In this instance, we’ll be using the web version of WhatsApp. This application will use a LevelDB to store information within the Chromium browser’s IndexedDB folder. There are other sites that are doing this as well including:
- Microsoft Office
- Google Docs
- Google Drive
- Google Photos
- Snapchat for Web
- Many…many others
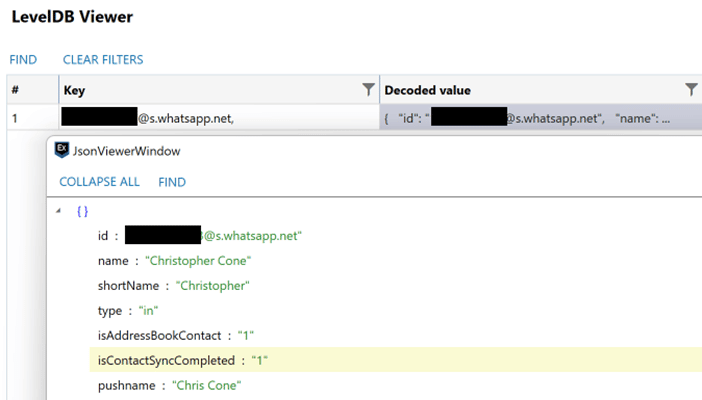
Digging inside the LevelDB for WhatsApp for Web (https_web.whatsapp.com_0.indexeddb.leveldb) we are presented with several things to look through including log data, contacts, conversation records, and even some message data. Unfortunately, the message content seems to be encrypted, but the rest of the information is decodable as JSON information. By starting with a generic search using the ‘FIND’ function in the LevelDB viewer, you can then target the returned data by doing a right-click and “View as JSON” option which will open a JSON viewer in a separate window.
Other data found within the LevelDBs can point us to logs stored within that show when the application was used and synced, conversation IDs can show us frequency of communication, and even some additional information around files that were transferred. As we continue to unravel these databases with our LevelDB Viewer even more may be uncovered. With the Chromium browser’s popularity in both general use web browsers but also application frameworks, I expect we’ll continue to see LevelDB files popping up in more and more examinations. Hopefully this tool can join the others in the AXIOM toolbox to help you deep dive data and find more evidence for your investigations.