
Harnessing the Cloud to Collect Off-Network Endpoints using AXIOM Cyber
AXIOM Cyber Customers can utilize AWS or Azure to collect from endpoints not currently on an internal company network. This also requires licensing of AXIOM Cyber via Cloud License Server (CLS). Check out our blog Three Reasons To License AXIOM Cyber in the Cloud to learn more about CLS and why it could be a good fit for your organization.
In this blog we’ll discuss how AXIOM Cyber customers can utilize AWS to collect an off premise corporate endpoint.
If you haven’t tried AXIOM Cyber yet, request a free trial here.
In order to accomplish remote collection from an off network corporate endpoint (Windows or Mac) using AXIOM Cyber, you’ll utilize AWS. With AWS, you must have two components in place. First, you will need to have an AWS EC2 instance running AXIOM Cyber with enough resources allocated to it to allow the collection to be stored on that instance and enough space, ideally on another attached volume to allow collected evidence to be processed. Secondly, you will need to have an appropriately configured Virtual Private Cloud with a Security Group that includes an inbound TCP rule that points to the public facing IP addresses on the endpoints that you will be collecting from.
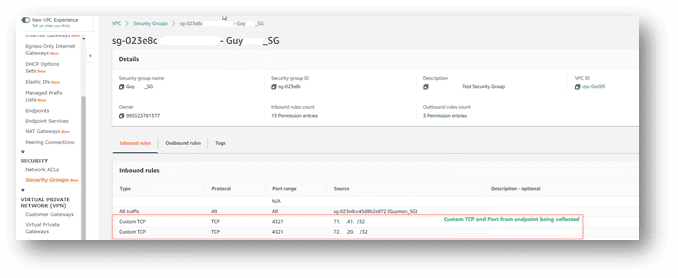
The screenshot below illustrates two example rules from the off premise, corporately owned endpoints that can be collected from using AXIOM Cyber via AWS. The TCP port is entirely up to you but must match the port used when creating the agent in a later step outlined below from within AXIOM Cyber.
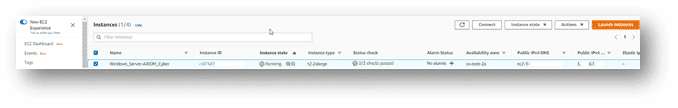
The EC2 instance used should have at least 32GB of memory, plenty of disk space and an appropriate number of vCPU’s to allow for processing of collected evidence. The example below is a “t2.2xlarge” instance type with 2 EBS volumes for the OS and collected evidence/case folder. However, a 3rd or 4th EBS volume could be used to separate the evidence and case folder as well as another for the AXIOM Process Temp folder, could be extremely useful to ensure processing is done as quickly as possible.
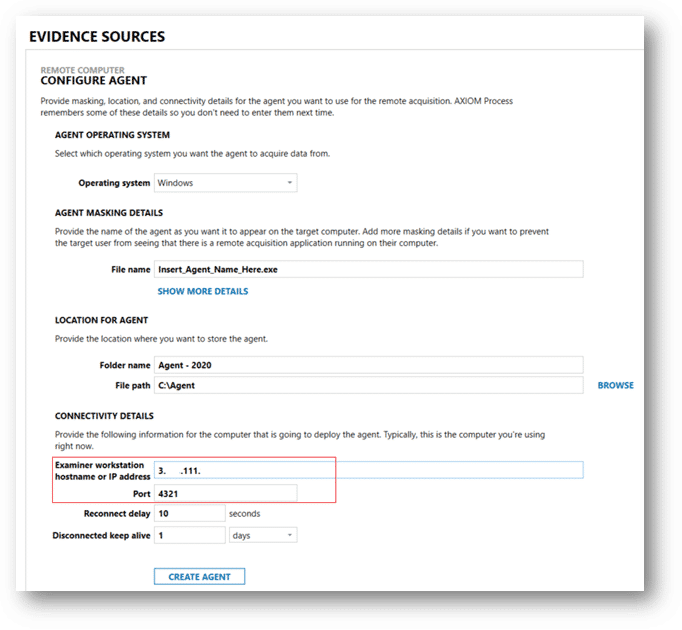
Once the Security Group inbound rule(s) and EC2 instance is available with AXIOM Cyber installed on it, the next step will be to open AXIOM Cyber Process and create an agent that will be used to collect from a remote, off premise corporate endpoint. The screenshot below illustrates this process. It is important that the agent be configured with the public facing IP address on the EC2 instance your created previously. It is also important that the TCP port used matches the inbound rule created in your Security Group above.
After the agent is created, it will be stored in the Agent directory in the EC2 instance where it will need to be copied and transferred to the endpoint via EDR or sneakernet utility where it can be executed in preparation to be remotely connected to. After the agent is running on the endpoint you wish to collect from, AXIOM Cyber can connect to the agent. Since the deployment was not done through AXIOM Cyber, that step is skipped and if the inbound Security Group rule is setup properly, AXIOM Cyber will connect to the agent successfully when the user selects “Connect to Agent”. This is illustrated in the below screenshot. You can now select your collection options.
NOTE: The local endpoint IP address will reflect the private IP of the endpoint being collected.
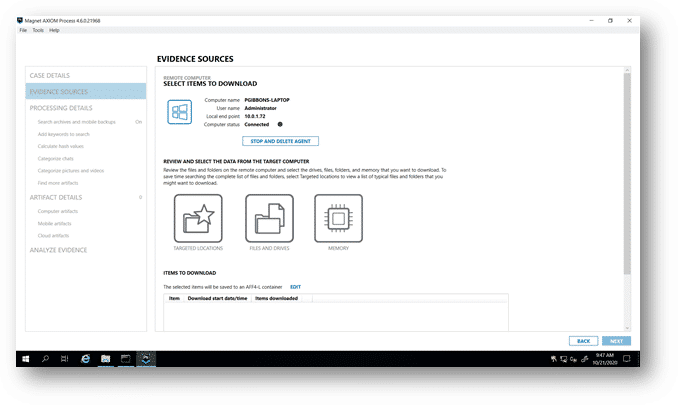
When selecting “Files and Drives”, the file system will be enumerated just as if you were collecting from an endpoint that was locally on your network. Both internal and external USB connected drives will be listed and available for collection.
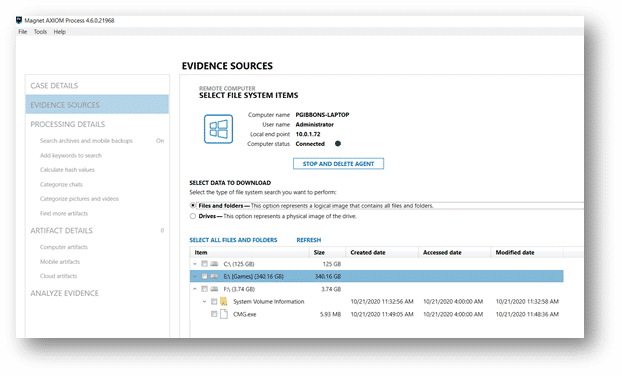
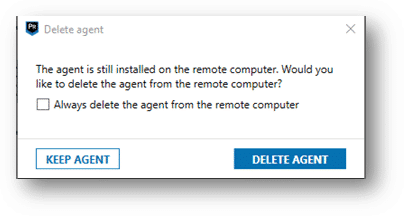
When you have successfully collected the evidence from the endpoint, you will be prompted to keep or delete the agent on the remote endpoint. Once selected AXIOM Cyber will continue with processing the evidence.
NOTE: Users can select evidence collected from endpoints be stored in either AFF4-L or .ZIP format. This is set within AXIOM Process settings before a collection.