Resources
Check out the latest resources and thought leadership.
Filter Content
By Product
By Topic
Featured content
Introducing Magnet One: Redefining the pursuit of justice
Recent blogs
Recent webinars
Recent white papers
Recent case studies
Start modernizing your digital investigations today
Ready to explore on your own? Browse our products
Start modernizing your digital investigations today.
Complete the company & contact information form below and sales will be in touch with you shortly.
Recent podcasts
Recent how-tos
Recent videos
Explore related products
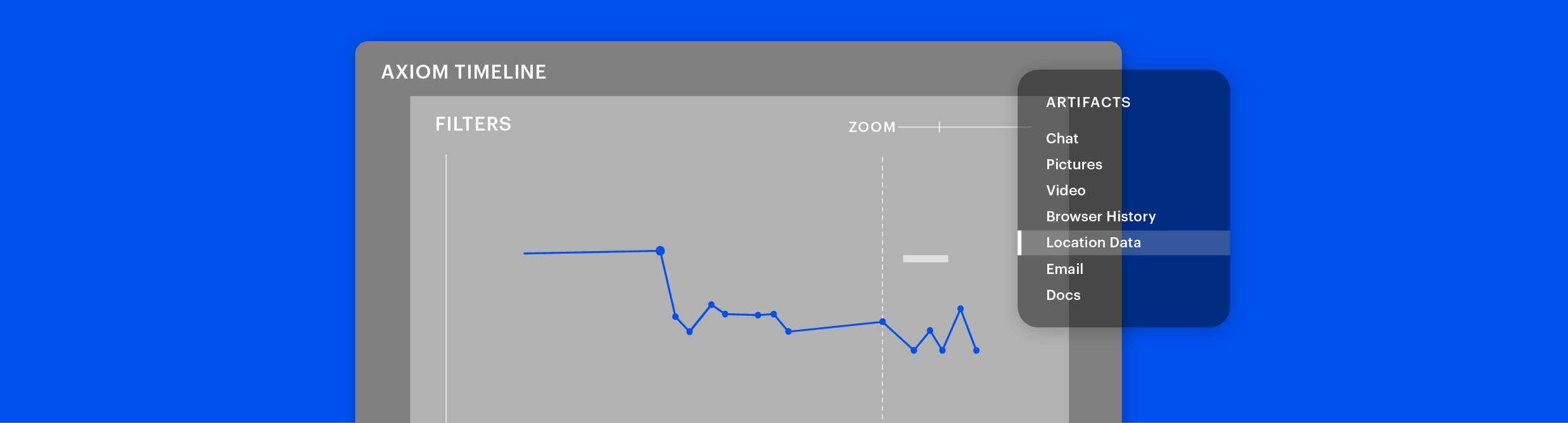
Examine and process digital evidence from mobile, cloud, computer, and vehicle sources all in one case file. Use powerful and intuitive analytical tools to automatically surface case-relevant artifacts and evidence quickly.
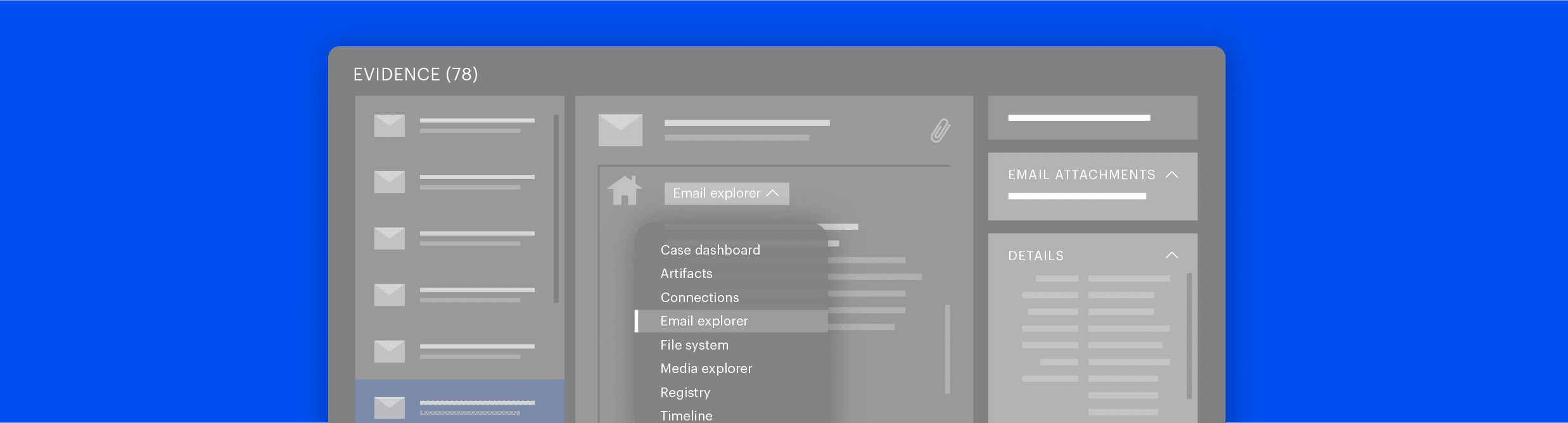
A robust digital forensics and incident response solution for businesses and organizations that need to remotely acquire & analyze evidence from computers, cloud, IoT, and mobile devices when faced with cyberthreats.
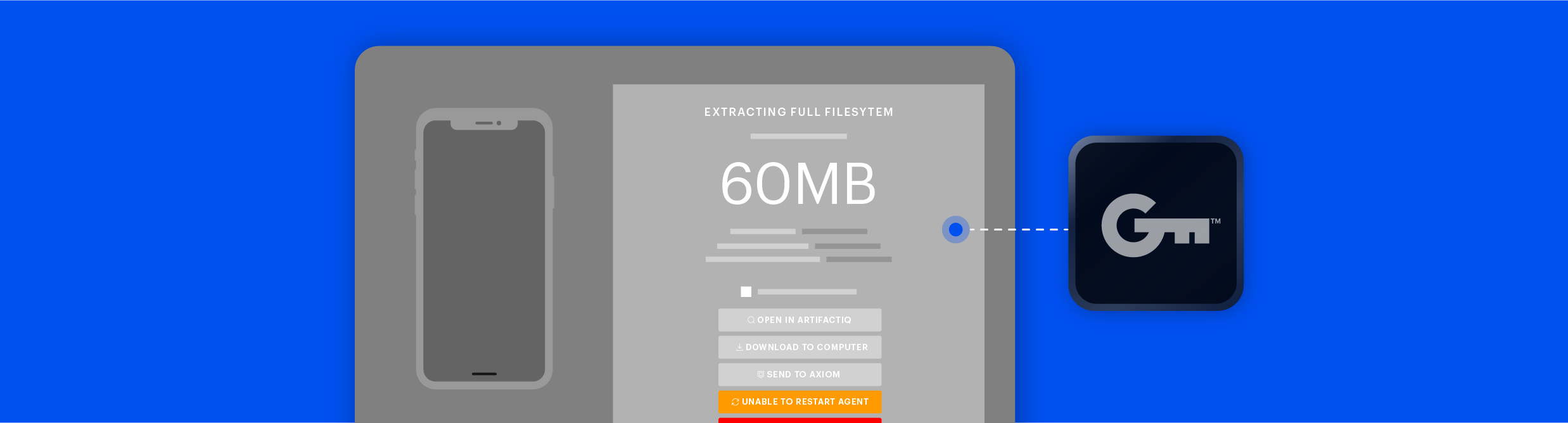
Lawfully access and extract encrypted or inaccessible data from the latest mobile devices & operating systems. Graykey accesses more data than any other extraction technology to help you solve cases faster.