Digital Forensics: Artifact Profile – Yik Yak

APPLICATION NAME: Yik Yak
CATEGORY: Chat
RELATED ARTIFACTS: Yik Yak Notifications, Yik Yak Yaks
OPERATING SYSTEMS: iOS
SOURCE LOCATION:
iOS – %root%\Library\Caches\engineering.locus.chatter\Cache.db
iOS – %root%\Library\Caches\engineering.locus.chatter\fsCachedData\%GUID%
Importance to Investigators
Yik Yak is a popular social media application most commonly used by young adults. The app, available on iOS and Android smartphones, allows users to post anonymous messages to other Yik Yak users within a five mile radius. While this is an entertaining concept for a social media app, Yik Yak is quickly becoming a new avenue for cyber bullying. This is especially true in areas close to schools, where students are anonymously posting hurtful things about other students without the risk of reprisal.
Recovering data from Yik Yak can be challenging since a lot of identifying information is not transmitted to the user or stored in the app. Even when examiners are able to recover the data from a device, identifying the user can be difficult as each user is represented by a unique GUID that reveals no identifying information. Those wishing to obtain more information on a user will likely have to request it from Yik Yak directly.
Despite not being able to obtain additional information about a user, the GUID is a unique identifier that allows examiners to correlate various Yaks or messages to a specific user.
Yik Yak Recovery with Magnet Forensics
Yik Yak Notifications
The first source of data for Yik Yak can be found in the Cache.db, which stores notification data of Yaks sent by other users along with an assigned status of read, unread, or new.
Magnet Forensics tools will:
- list the content of the message (which is often called a “Thing” by Yik Yak),
- the user ID of the user who sent the “Thing”,
- the status of the message,
- a timestamp for when the notification was created, and
- several other identifiers that may be useful to the examiner depending on the case.
It is important to note that notifications in Yik Yak can come from a multitude of users and don’t generally represent direct messages or interactions with a specific user. The notifications might have been sent to the user because they were in the same geographical area.
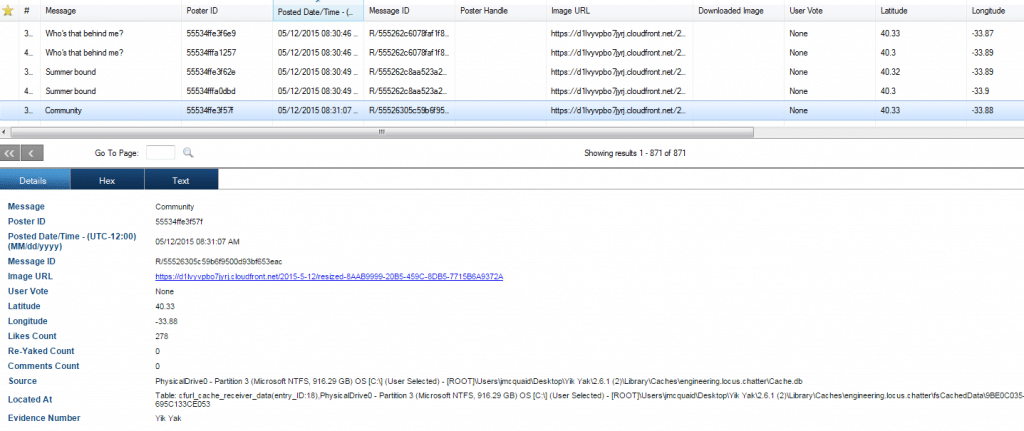
Yik Yak Yaks
Yaks are the messages that people post to their locale in Yik Yak. Much of this data is stored in a JSON format. iOS devices will store:
- the message,
- the poster ID (much like the user ID for notifications, this is unique but does not contain any identifiable information on the actual person who sent the Yak),
- a timestamp of when it was posted, and
- some additional metadata about the message.
One thing that was identified in our testing was a single Yak may be duplicated with multiple poster IDs. We are unsure what creates this, but it appears to be something that Yik Yak does without the individual user interaction. The Yak may also contain a link to a picture if one was included in the Yak. Often times the pictures in the links cannot be viewed outside the application due to a private key stored in the app.
The Yaks also contain the latitude and longitude of the area where the Yak was sent.
NOTE: This is not an exact geolocation of where the user was when they posted the message. In our testing, this location represents the general area where the message was sent and therefore should not be used to indicate an exact GPS location of the user. Rather, it can be used as a guideline to indicate the general area where the messages were being sent and received.
Below is a screenshot of the type of data retrieved using Magnet Forensics tools:
Overall, there is a good amount of data to be pulled from iOS devices for Yik Yak. Most of this data is found due to the way iOS stores and caches its data. This causes some issues when attempting to analyze Yik Yak data on Android since the storage methods on an Android device aren’t as robust and limit what data is available to the examiner.