Anatomy of A Ransomware Investigation
Organizations must be prepared to swiftly perform a forensic analysis from the moment that they are aware a ransomware attack has occurred.
In this post, we’re following a realistic, yet hypothetical ransomware investigation picking up where the forensics lab would begin and end its work.
This article has been authored by experts at Magnet Forensics who have worked ransomware investigations in their roles as examiners in the past. As much as possible, we’ll provide a sequential chronicle of events. Although if you’ve ever performed a ransomware investigation, you’ll know that not everything happens nicely in order.
But to investigate a ransomware attack effectively—especially when tensions are high, and the pressure is on during an actual attack—it’s imperative to understand the timeline of a ransomware investigation and how digital forensics tools can help support your incident response efforts.
After all, the stats are alarming when it comes to ransomware:
- Experts estimate that a ransomware attack will occur every 11 seconds in 2021.1
- Since 2016, over 4,000 ransomware attacks have happened daily in the U.S.2
- The average ransom fee requested has increased from $5,000 in 2018 to around $200,000 in 2020.3
- The average cost to recover from a ransomware attack is $1.85 million.4
- In September 2020 alone, cybercriminals infiltrated and stole 9.7 million medical records.5
- 90% of financial institutions have been targeted by ransomware attacks.6
And unfortunately, the list goes on and on and on.
Let’s see how a ransomware investigation can be done.

Forensics lab gets an alert from the SOC of potential ransomware attack and is asked to validate
Depending on the size of company, thousands or even millions of security events (possible indication of compromise) can get logged in a day. The alert may turn out to be nothing, a false positive, or it may indeed turn out to be an actual ransomware attack.
The reality is that every alert like this must be given the seriousness and urgency that it is an actual ransomware attack. And speed is definitely of the essence when validating an alert like this!
The forensic tools that you use must be fast, and they must be accurate. Oftentimes, based on the alert or notification that kicks off your investigation, you’ll know what it is that you’re looking for, such as a file name for example. And you’ll know what device or endpoint you’re investigating based on the alert too.
To validate the alert, a quick scan or triage of an endpoint is needed to verify (or hopefully invalidate) the alert. A triage tool like Magnet IGNITE can scan for malicious activity or individual keywords on target endpoints—even multiple ones simultaneously.
Things to keep in mind:
- Notifications can come from many different places aside from the SOC. Some other sources include appliances, alerts from other systems, and even outside sources.
- Ensure to validate notifications swiftly to determine whether or not they need further action.

Triage results confirm ransomware attack, now it’s time to enact your incident response plan
After you’ve confirmed that a breach has occurred and the suspected ransomware attack is, in fact happening, a lot of things are going to start happening at once. It’s going to be stressful, and the forensics lab is going to be integral in performing root cause analysis. Answers that you dig up from a deeper forensic analysis of infected endpoints or devices will arm other cross-functional teams with the information they need to do their jobs.
Some of the most important teams you’ll immediately want to connect with are your various Security teams—including but not limited to Network, Cloud, or Endpoint Security—so they can as quickly as possible isolate and quarantine infected endpoints and servers, even network segments, to mitigate the spread of the ransomware attack.
Other internal teams you’ll be working with may include Marketing or Public Relations for external communication, Legal to understand what responsibilities your organization has, HR so you can connect with the employee who triggered the attack. Even something as simple as understanding what application they were using when they initiated the attack can be extremely valuable.
External teams may be engaged as well such as your cybersecurity insurance provider and relevant regulatory bodies. Depending on the size and scope of the attack, you may want to consider engaging law enforcement. In the U.S., that would be the Secret Service and/or the FBI.
Things to keep in mind:
- Built into your incident response plan needs to be a communication plan too
- Having a single point of contact that can liaise with other groups while the forensic team is performing their root cause analysis streamlines activities and allows everyone to focus on what they need to do
- Your cybersecurity insurance provider may have specific vendor requirements or steps that you need to take to keep your policy valid. If these steps aren’t built into your IR plan—which they should be—then be sure to take the appropriate actions.

Perform root cause analysis while preserving evidence
There are going to be a barrage of questions that need to be answered:
- How did we get hit?
- How many endpoints got hit?
- What was lost?
- What was the customer impact?
- Was customer data or PII taken?
- Are we secure now? Is it over?
And many of those answers are going to be coming from the forensics lab.
Getting the answers you need though may prove to be challenging, the endpoint that you’re investigating is now most likely encrypted. The average time it takes for ransomware to start encrypting files is three seconds.7
Therefore you’re going to be relying on data from many different sources:
- From the infected endpoint you’ll want to start by collecting the volatile memory in addition to the full disk image
- Pull the most recent backups or snapshots of the infected endpoint. If they haven’t been encrypted, they can be a vital source of evidence
- Acquire any system logs that you can. Specifically, Window Event Logs and Firewall Logs. The Volume Shadow Copy is another very good resource to look for evidence, if it hasn’t been encrypted
- Log files from all the different appliances (e.g. CrowdStrike, Blue Coat, etc.) that caused the alerts to go off
- Network traffic going to and from the infected endpoint
The forensic tool at your fingertips should be nimble, powerful, and easy to use. These characteristics will enable you to act with both speed and precision. We believe Magnet AXIOM Cyber fits the bill very well to perform root cause analysis for ransomware investigations.
Here are a few ways that AXIOM Cyber specifically can help with your ransomware investigation:
- Powerful analytics features can reduce your time to evidence:
- Connections will visually show you how a file, a malicious payload for example, originated and where it went and how it got there.
- Timeline will quickly establish an easy-to-follow timeline of events determining timestamps of infection and possibly patient zero.
- You can analyze Linux artifacts coming from servers or other devices within your network that will help identify network traffic going to and from the infected device giving you clues as to how the attacker moved through your network and possible what other endpoints may be infected.
- Remote acquisition of target endpoints can be performed, even when they’re not connected to your corporate network via VPN. Watch this video to see how you can perform remote acquisition of an off-network endpoint with AXIOM Cyber.
- Capturing and analyzing RAM/memory will be imperative to understand what happened on the infected endpoint.

Ensure your security perimeter is free from ransomware before network restoration
On average, ransomware attacks cause 15 business days of downtime. Due to this inactivity, businesses lost around $8,500 an hour.8 Therefore, there is a real urgency to safely get the business fully operational again.
At this point what you’re primarily concerned about is any cross-contamination of uncontaminated network segments or endpoints with the quarantined assets that you’re preparing to bring back online.
Restoration will definitely be a cross-functional effort, however the role that the forensics team may play in the process will be to inspect and validate those traces of ransomware and IOCs are gone and that any backdoors that attackers may have installed are removed as well. A study by Cybersecurity firm Cybereason shows that more than half of respondents were hit with a ransomware attack and 80 percent of those who paid the ransom were hit with a second attack, often by the same thief.9
Before you bring isolated endpoints and network segments back online, you’ll want to use AXIOM Cyber to do a sweep for IOCs or remnants of the ransomware on the image that you will be using as your base or gold image.
Some common places that attackers like to plant backdoors that they may use in future attacks are Active Directory and email servers.
Things to keep in mind:
- Ransomware often targets backups too; your backups should be inspected prior to restoration as well.
- Use this as an opportunity to get up to date on all of your patching and server updates
- One quick way to identify what’s different on an endpoint is to load a gold image hash set into AXIOM Cyber and then compare it against the endpoint you’re investigating. To see how it’s done, read this blog post Building a Gold Build Hash-Set for Use in Magnet AXIOM, which also includes a video walkthrough.

Produce your report and be prepared to debrief so lessons learned can be incorporated into the incident response plan
The dust has settled. The infected endpoints have been safely and successfully restored. Ransomware has been eradicated from your network.
Now it’s time to report on your investigation so valuable lessons learned can be realized and then incorporated back into your incident response plan to hopefully prevent a similar kind of incident from occurring again in the future.
When putting together your report, one of the most effective ways to go about presenting your findings is by showing a timeline of events. AXIOM Cyber has a feature called Timeline that will rebuild the sequence of events with timestamps during the incident in an easy-of-follow way.
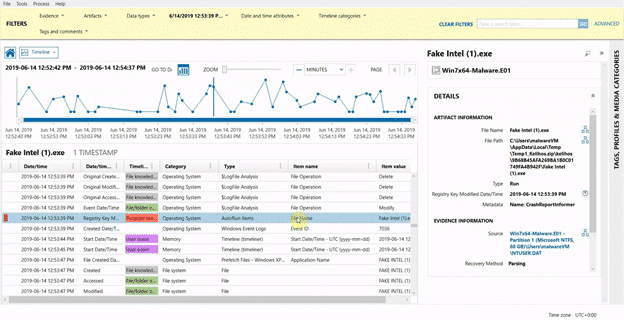
When using Timeline, you can then pick and choose what you want to include in your final report taking screenshots along to way to support your evidence.
Another feature of AXIOM Cyber that can help you build your report is Connections. Especially important for an investigation such as ransomware which will follow a file as it moves from device to device within your network. You’ll have an idea of where, how, when a file was moved helping to pinpoint how many endpoints may have come in contact with the ransomware payload.
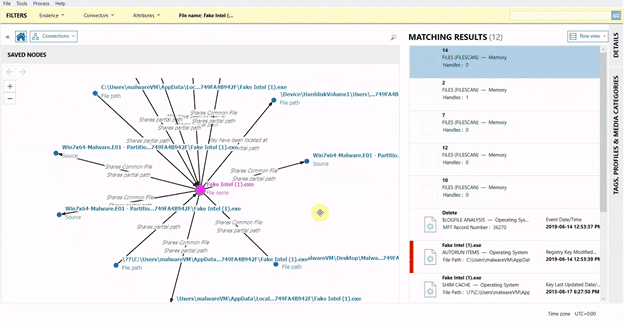
Armed with that information you’ll be able to succinctly summarize the steps taken to analyze and then inspect those infected endpoints.
Things to keep in mind:
- You’ll have documented all of your steps and tasks that you’ve taken throughout the course of your investigation, this is where those notes will come in handy to demonstrate what you did
- Your report will most likely be consumed by many different stakeholders, technical ones as well as non-technical ones, try to take both audiences into consideration when writing your final report: avoid jargon, acronyms, and try to write plainly
- Be prepared to be debriefed in a post-mortem interview one-on-one or in a group setting
That’s it. While we hope that you never have to perform a ransomware investigation, it’s good to be prepared and have the right toolset at your fingertips to act as quickly as possible. And while there are several different tools that you’ll use throughout an entire lifecycle of a ransomware attack, AXIOM Cyber can be an integral part of your road to recovery.
Learn more about Magnet AXIOM Cyber and request a free trial to see how it can help you with all of your corporate digital forensic investigations.
Citations
- [1] https://cybersecurityventures.com/global-ransomware-damage-costs-predicted-to-reach-20-billion-usd-by-2021/
- [2] https://www.justice.gov/criminal-ccips/file/872771/download
- [3] https://www.nsi.org/2021/02/15/employee-cyber-security-awareness-ransomware-wave/
- [4] https://www.sophos.com/en-us/medialibrary/pdfs/whitepaper/sophos-state-of-ransomware-2021-wp.pdf
- [5] https://www.hipaajournal.com/september-2020-healthcare-data-breach-report-9-7-million-records-compromised/ [6] https://www.prdistribution.com/news/financial-institutions-90-of-them-have-been-targeted-by-ransomware/3279096
- [7] https://enterprise.comodo.com/blog/how-fast-does-ransomware-work/
- [8] https://healthitsecurity.com/news/ransomware-causes-15-days-of-ehr-downtime-as-payments-avg-111k
- [9] https://www.pymnts.com/news/security-and-risk/2021/cybereason-study-80-pct-of-ransomware-victims-that-pay-get-hit-again/
Further Reading
Technical Advice Disclaimer
Magnet Forensics is dedicated to engaging with the DFIR community through our blogs and whitepapers. However, properly addressing technological issues often includes numerous variables that require independent assessment and strategies designed for each specific circumstance. Since Magnet Forensics cannot have complete insight into all variables involved in a specific situation, this blog/whitepaper is for informational purposes and should not be read as professional advice recommending techniques or technologies to address your specific situation. We do not accept responsibility for any omission, error, or inaccuracy in this blog/whitepaper or any action taken in reliance thereon.